CASE STUDY
A Ghost Attacker in RAM: Neutralizing a Fileless Breach
Background
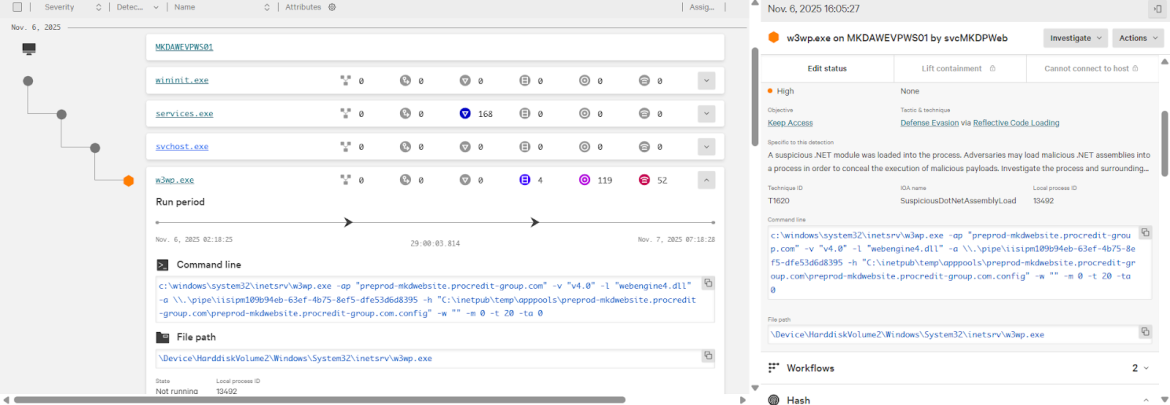
In early November, CrowdStrike Falcon detected suspicious activity on one of our customer’s production servers. A high-severity alert showed the IIS worker process (w3wp.exe) repeatedly loading a .NET module (webengine4.dll) — a pattern that demanded immediate investigation.
From the very first trigger, our engineers recognized the alert’s nebulous nature, which raised a red flag. The automated data lacked immediate context and involved a legitimate, signed Microsoft DLL. From our team’s experience, ‘nebulous’ signals are often the preferred cover for sophisticated actors.
The alert persisted over time and appeared across multiple application pools. Between 14:04 and 15:35 UTC on November 6, the same DLL was loaded more than 20 times in rapid succession. CrowdStrike classified this behavior as Defense Evasion via Reflective Code Loading, raising concerns that this might not be a simple misconfiguration or application bug.
So, was this an IIS glitch or a stealthy, fileless attack designed to blend into normal server behavior?
The Challenge
ASP.NET ViewState is a built-in mechanism used by ASP.NET Web Forms applications to preserve page state between HTTP requests. To prevent tampering, ViewState data is protected with machine keys. These keys act as a trust anchor between the client and the server.
Years of lazy development habits have created a goldmine for attackers. Ctrl+C, Ctrl+V applied to machine keys straight from public docs, code repositories, and code examples has become a common practice among developers. The moment those keys hit the public domain, attackers can weaponize them to forge ViewState payloads that servers trust implicitly.
In December 2024, Microsoft caught attackers exploiting this weakness in real attacks. They were using publicly disclosed ASP.NET machine keys to inject malicious code through ViewState. This allowed them to execute attacker-controlled .NET assemblies directly in memory within IIS worker processes. Microsoft found over 3,000 publicly exposed machine keys. The warning was clear: these keys dramatically increase the risk of ViewState code injection attacks, especially when developers reuse them across multiple environments and applications.
These attacks are particularly dangerous because they are fileless by design: no malware binaries are written to disk, no web shells are dropped, and traditional IOC-based detection often fails. All malicious activity occurs directly in memory, making visibility and contextual analysis critical.
About the client
UnderDefense MAXI
Key Results
The Solution
Our security engineers had already initiated a deeper investigation, prioritizing process-level telemetry while the alert was still in its earliest, most ambiguous stage.
Initial validation confirmed that:
- webengine4.dll was a legitimate Microsoft library,
- file hashes were intact,
- no malicious files or web shells were present on disk.
Despite this, the recurring reflective loading behavior remained unexplained.
Following our initial detection and isolation of the threat, CrowdStrike Falcon OverWatch, a human-led threat hunting team, joined the investigation. Their analysis revealed that similar malicious .NET activity had been observed across multiple CrowdStrike customers worldwide. The activity was attributed to a malware family known as Sharp ViewState King, which abuses ASP.NET ViewState to execute attacker-controlled code entirely in memory.
OverWatch confirmed that the malicious payloads never touch disk, all execution occurs within the IIS worker process memory, and traditional file-based forensics would not reveal the attack.
OverWatch provided two specialized LogScale queries:
- A query detecting reflective loading of .NET assemblies into w3wp.exe.
- A query exposing ScriptContentBytes, allowing visibility into the actual injected payloads residing in memory.
Using these queries, our team confirmed the presence of multiple injected .NET assemblies with different hashes. This was clear evidence of malicious code execution rather than benign IIS behavior.
Complete Incident Timeline
Late October
Low-frequency but recurring reflective .NET loading events begin appearing across multiple IIS application pools.
November 6, 14:04 UTC
Surge in reflective loading activity detected in w3wp.exe. Same DLL (webengine4.dll) loaded repeatedly within a short time window.
November 6, 15:35 UTC
CrowdStrike raises a high-severity alert for defense evasion via reflective code loading.
Initial Analysis
- DLL verified as legitimate and untampered.
- No suspicious files or persistence mechanisms found on disk.
Escalation to Falcon OverWatch
- OverWatch correlates activity with global telemetry.
- Attack attributed to the Sharp ViewState King malware family.
Deep Memory Analysis
- LogScale queries reveal multiple injected .NET assemblies in IIS memory.
- ScriptControlScanTelemetry events expose in-memory payload content.
Payload Validation
SHA-256 hashes confirmed the presence of offensive tooling, including:
- MachineKeyExtractor
- ExecuteAssembly
- LoadLibrary
- Root Cause Identified
ViewState code injection enabled by a compromised or publicly disclosed ASP.NET machine key.
Outcomes
Working through the case, our engineers:
- Detected and contained the fileless intrusion before the attacker could escalate privileges or establish persistence.
- Confirmed the attack was executed entirely in memory, with no malicious files or artifacts written to disk.
- Identified the compromised ASP.NET machine key and rotated it to immediately disrupt the attacker’s execution path.
- Deployed additional monitoring rules to detect reflective .NET assembly loading and ViewState abuse within IIS worker processes.
- Provided the customer with full visibility into a highly evasive attack that would have otherwise blended into normal IIS behavior and remained undetected.
Our Recommendations
-
To secure the environment and prevent future exploitation, our MDR team recommended taking the following strategic steps:
- Rotate All ASP.NET MachineKey Values
Generate new, strong, randomly generated validationKey and decryptionKey values. Apply MachineKey rotation to all applications that may share inherited or duplicated keys. - Enforce Strong ViewState Security Controls
Enable ViewState MAC and ensure enableViewStateMac=“true”. Set ViewStateEncryptionMode=“Always”. Disable legacy ViewState compatibility modes if still enabled. Validate that the machineKey is set to secure algorithms. - Rebuild and Harden the Affected IIS Server
Reapply application code through a clean deployment pipeline. Revoke any cached credentials or tokens stored on the server. - Secure Application Pools and Execution Environment
Change the password for the IIS service account PCGsvcMKDPWeb. Enforce least-privilege rights for all IIS worker process accounts. Disable unnecessary application pools, ISAPI modules, and handlers. - Patch and Update All IIS and .NET Components
Ensure all relevant IIS, ASP.NET, and .NET Framework security patches are applied. Confirm that the server is running the latest supported version of the .NET Framework. - Implement Web Application Firewall Protections
Enable or strengthen WAF rules: suspicious payloads in POST/GET parameters, large or anomalous Base64 input patterns. Consider adding custom rules to detect exploitation signatures similar to the ones used here.
7. Enable Enhanced Logging and Monitoring
Enable detailed IIS request logging (including POST data, if permitted).
How UnderDefense MAXI Builds Ultimate Security
UnderDefense specializes in detecting and investigating stealthy, fileless malware attacks that bypass traditional security controls. Our UnderDefense MAXI platform provides deep process-level visibility and rich contextual telemetry strengthened by human expertise capable of interpreting ambiguous signals and uncovering hidden attack techniques.
This hybrid approach allows us to identify threats that look like “normal system behavior” at first glance.
The post A Ghost Attacker in RAM: Neutralizing a Fileless Breach appeared first on UnderDefense.